Engineering the Wireless Hospital: Client Device Requirements
Published on June 24, 2013

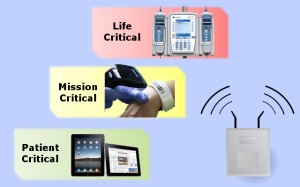
Client Devices in a Hospital
By: Natalie Sheerer, Marketing Specialist
In a recent post, we introduced a Wi-Fi Alliance® white paper on improving the user experience for client devices that use Wi-Fi® to connect to hospital networks. According to the paper, hospital IT managers should consider client device requirements before designing or updating Wi-Fi networks. Different types of client devices have different requirements because they run different types of applications and serve different types of users.
One important set of client devices is hospital-managed devices, because Wi-Fi in a hospital must provide those devices with access to applications and data on the hospital’s networks. Hospital-managed client devices include:
- Computing devices such as computers-on-wheels (CoWs), tablets, laptops, desktops, and mobile computers
- Medical devices such as patient monitors, patient diagnostic tools, and infusion pumps
When compared to computing devices, medical devices send and receive much less data over Wi-Fi. But the data sent (and received) by medical devices is critical to patient wellness and care. Hospital IT staff must design and configure hospital Wi-Fi networks to ensure that every packet of data that is sent or received by a medical device reaches its destination quickly or applications that run on medical devices may be disrupted.
Another set of devices that use Wi-Fi in a hospital is the personal computing devices – primarily smartphones and tablets – of doctors, nurses, and other caregivers who work in a hospital. Most hospitals have liberal “bring your own device” (BYOD) policies, and so caregivers in a hospital expect to be able to use Wi-Fi on their personal devices to connect to applications and data on hospital networks.
Unlike hospital-managed devices, personal devices are not configured by hospital IT, and hospital IT cannot depend on caregivers to configure their own devices to adhere to hospital policies for Layer 2 (WPA2-Enterprise) security and quality of service (QoS). If hospital IT allows personal devices to connect with different Layer 2 security than that used by hospital-managed devices, then devices of patients, guests, and others may gain access to the same Wi-Fi networks and, through them, protected information, including patient information, on hospital systems.
To avoid the need to add additional (Layer 3 and above) security measures behind all access points in a hospital, most hospital IT professionals opt to treat BYOD devices like the devices of patients and guests. When caregivers want to gain use their personal devices in a hospital, they connect to a guest Wi-Fi network that provides Internet access – not direct access to hospital systems. Caregivers then use their devices as if they were remote to the hospital, with all security handled at Layer 3 (VPN) or above (application-level security). One downside of this approach is that caregivers’ devices must compete for Wi-Fi bandwidth with the devices of patients and guests.
 Laird Connectivity is now Ezurio
Laird Connectivity is now Ezurio